Does this quote sound familiar?
“The electric automobile will quickly and easily take precedence over all other kinds of motor carriages as soon as an effective battery of light weight is discovered.”
That’s the Los Angeles Times in 1901. How about this one?
“Prices on electric cars will continue to drop until they are within reach of the average family.”
That’s the Washington Post, 1915.
At Substack, Robert Bryce headlines: “Tesla In Turmoil: The EV Meltdown In 10 Charts.” The electric vehicle bubble is bursting, with Tesla, the only semi-successful EV manufacturer so far, in trouble. Its stock price has fallen 41% this year:
Tesla is the bellwether for the EV business, and it’s in trouble. Last week, the company announced it was laying off more than 10%, or about 14,000, of its employees. The move comes after a quarter during which the company missed delivery expectations and just before it reveals its quarterly profits on Tuesday. Here’s what Wired wrote last Thursday about Tesla’s situation: “Demand is dropping for electric cars in the U.S. and Europe, just as competition in China intensifies and workers revolt in Europe. Investors are worried.”
There are now murmurings that Tesla could go bankrupt. I like Elon Musk, and we need him: I fervently hope that he has gotten most of his money out of Tesla.
Robert offers a series of charts that document the problems the EV industry is facing. Sales of EVs (55% of them Teslas) are concentrated in a few states and a handful of very blue counties. Fewer vehicles are being sold overall, and an increasing number of Americans say they won’t consider buying an EV. One reason why consumers don’t want to buy EVs is that they understand charging them is a permanent problem that will prove insoluble if government mandates are actually enforced. Thus:
In 2019, Southern California Edison, one of the biggest investor-owned utilities in California, estimated the amount of juice needed to electrify transportation in the state. The utility found that trying to do so “will increase electric load by nearly 130 terawatt hours — representing more than one-third of the grid-served load” by 2045. The same report estimated the state will need to add at least 80 gigawatts of new zero-carbon electricity generation capacity over the next two decades. But … California’s electricity use is falling. Some of that decline is due to people and industry leaving the state. The other factor may be the high cost of power in the state. Further, California will not add 80 GW of new generation capacity over the next 20 years. The permitting process is far too long, and the costs of trying to do so are too high.
Electric vehicles will always be much more expensive than internal combustion vehicles because they need vast quantities of raw materials:
EVs require massive amounts of metals, minerals, and magnets. This chart uses a screengrab from a 2021 report by the International Energy Agency called “The Role of Critical Minerals in Clean Energy Transitions.”
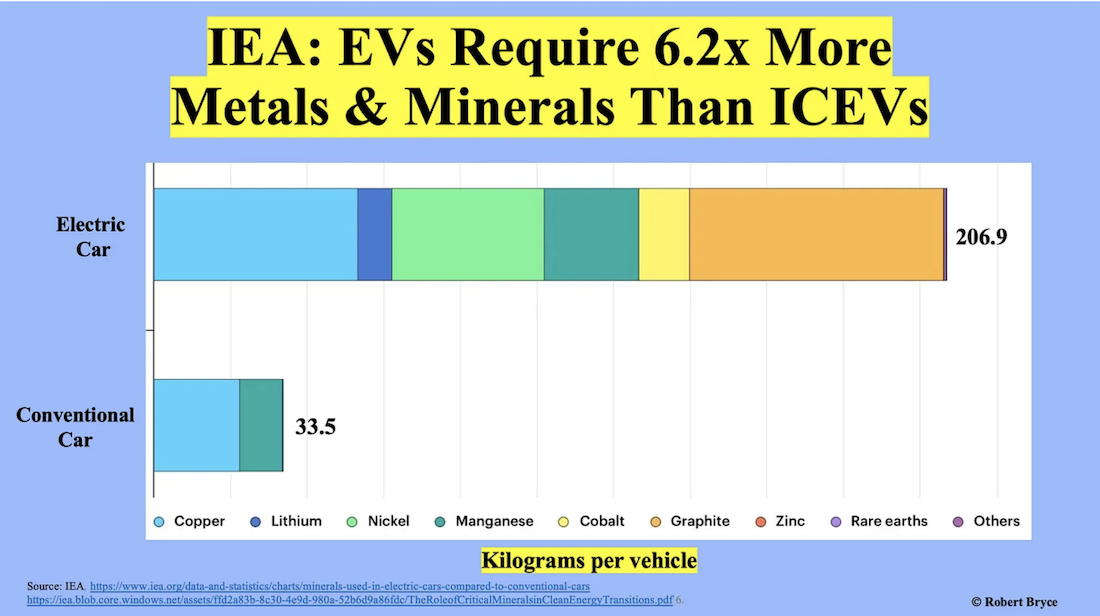
What’s worse is that we depend on the Communist Chinese for those materials:
Last month, the Biden Administration finalized rules requiring U.S. automakers to slash the number of internal combustion-engined vehicles they produce. By 2032, about 60% of the cars they sell must be fully electric. Why, in the name of Jesus, Mary, and Joseph, is the Biden crowd so eager to make our auto sector dependent on Chinese supply chains?
This chart tells the story:

Then, worst of all, we have magnets:
Last May, in “The EPA’s China Syndrome,” I explained how the proposed mandate on EVs would make the U.S. dependent on China for “neodymium-iron-boron (NdFeB) magnets. Those magnets are critical components in electric vehicles and wind turbines as well as in military applications like ship propulsion systems and guided-missile actuators.” The EPA has completely ignored the magnet supply issue. In fact, the word “magnet” doesn’t appear one time in the agency’s 1,200-page final tailpipe rule.
This is pure foolishness. In 2022, the Commerce Department issued a heavily redacted report on Chinese magnets and the threat they pose to our security.

And of course all of this gets vastly worse if we also try to transition our power system from fossil fuels to wind and solar.
But let’s go back to Robert’s question: why is the Biden Administration trying to turn our future over to the Chinese Communist Party? One explanation is that Biden was the Manchurian Candidate, and the millions of dollars the Chinese have paid him and his family have put him in their pocket. That seems hard to believe. But what is the alternative explanation?
Then we come to the availability of needed natural resources. Apart from the fact that the Chinese control the current supply, we have the question: how will the vastly increased demand for raw materials be met?
[I]f [Richard Herrington, the head of earth sciences at the Natural History Museum in London, and seven colleagues’] numbers are right, electrifying all of U.S. motor vehicles would require roughly 18 times the world’s current cobalt production, about nine times global neodymium output, nearly seven times global lithium production, and about four times world copper production. Even if there were sufficient political will — and money — to attempt an electric overhaul of the transportation sector, there may not be enough cobalt or rare earth elements to meet demand.
And that is just for the U.S. Western European countries are electrifying (or pretending to electrify) their automobile fleets, too. And you could do a comparable calculation for the alleged transition from fossil fuels to wind and solar energy. Even if you assume that the Earth somewhere holds enough raw materials to meet this enormous demand, the mining, manufacturing and transportation effort needed to carry out these mandates would be the greatest since the Industrial Revolution. And how much of that mining do you think would take place in the U.S.? Little or none, under current political conditions.
Electric vehicles are a novelty item and have been for over a century. There is no way that our automobile fleet will be converted from internal combustion to batteries, just as there is no way we can or will replace fossil fuels and nuclear power with wind- and solar-generated electricity. The whole thing is a fantasy. But the damage that will be done to our economy, our livelihoods and our national security, in pursuing that fantasy, is incalculable.




